How to do login testing using Hakku Framework?
The Hakku framework is an open source testing platform. It can be used to perform web and network-related login assessments, such as data collection and risk assessment activities. The framework has many modules divided into the following groups. Hakku Framework is a information gathering tool, its collect all information related to target.
For example
1) Web Modules
2) Network modules
3) Wireless and Bluetooth modules
4) File modules
5) Generator Modules
Web and Network are the major modules of the Hakku framework. Web modules are closely related to data collection. Most network modules can be used for network testing (risk assessment). Wireless & Bluetooth contains wifi jammer and Bluetooth attack modules. In addition, the framework contains integrated entry testing tools; such as list generators and utilities (Zip, Rar) for file fragmentation.
How to install Hakku Framework?
Hakku Framework is a Python3 framework designed for Linux applications. The framework can be compiled from Github using the following command.
git clone https://github.com/4shadoww/hakkuframework
It is github link to cloning hakkuframework in termux and linux.
hakku framework cloning
After assembling the Hakku, navigate to the draft directory using the following command.
cd hakframework
ls
list of hakku texts
The Hakku Frame is a portable device that does not require any installation to be performed. However, input files exist in the main directory if installation is required. The following instructions can be used to insert a draft.
chmod + x * "enter # permission to change the file"
./install
The module folder contains the text of the pre-loaded modules. Make these text files usable using the following instructions.
modules cd
chmod + x *
hakku module list permission update
The Hakku framework does not have specific package requirements. Python3 provides all the libraries required for the framework of use. The following command shows all the dependencies (pre-completed) required for different framework modules.
dependent list
How can you use the Hakku framework?
The following command opens the Command Line Interface (CLI) framework.
python3 hakku
Type <help> in the terminal to check all the essential instructions needed to use the draft.
Help
there is no help command
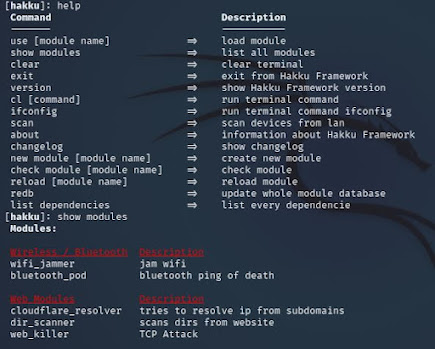
The [show modules] command lists all available modules in the following format.
show modules
As we can see in the screenshot above, the web, and network modules dominate the framework. We can use each module by typing the following syntax.
use <module name>
Example of a web module
Port_Scan: Suppose we need a hole scanner module to find open holes for a web site (webscantest.com). We can select the port_scanner module using the following command.
use port_scanner
Type <help> in the terminal for a general view of the module commands.
Help
hole scanner help command
The <show options> command shows all the required parameters and options.
show options
show options command
There are three parameters that you must configure before using the hole scanner module. The [target] parameter defines the target domain. The [first] and [last] parameters indicate the width of the holes to be scanned at work. We can set these parameters as shown in the following screenshot.
port scanner settings
The <run> command launches the hole scanner module to scan the pre-defined width of the holes. Results are displayed in the following format.
living ports
Although the port scanner module is associated with web domains, we can use the module to scan network servers.
set a target
open metasploit ports
Example of a network module
Network_kill: Similarly, we may use the network_kill module to block connections between a router and a targeted network machine. Such an attack was introduced to force the targeted devices to connect to an unreasonable access point. The command to select a module is the same for all tasks.
use network_kill
The <show options> command indicates the required parameters.
Network kill options
We need targeted and router IP addresses in order to launch a network_kill attack. We can use various tools like Nmap to get targeted IP addresses. At localhost, we can use the following command to find the router's IP address.
route -n
router ip check
After setting the route and the target IP address, use the <run> command to block the connection between the route and the target machine.
network kill settings and effects
Conclusion
The Hakku Framework tends to meet the basic entry test requirements. The open source framework allows you to customize available tools. The framework also allows developers to add new modules to the framework website.